Online Privacy Improved with SameSite Cookie Attributes
The latest big idea to help tame the insecure world of browser cookies is using SameSite cookie attributes. Learn more about the attributes and Google Chrome's recent warning signs.

Online privacy has been in the spotlight for quite some time and will continue to be in the future. Web cookies are continually being discussed and security measures are actively taking place to prohibit the misuse of a cookie.
The most common use for cookies is user identification (a site stores a user’s ID after leaving the page). Cookies look simple on the surface – they’re a little chunk of text data that a website can ask your browser to remember. However, the small website cookie has powerful controls.
There are pros and cons of cookies – the pros tie to websites delivering personalized user experiences based on tracking behaviors, and cons relate to using personal data maliciously or hacking a user’s profile.
The latest big idea to tame the insecure world of browser cookies is an IETF standard called SameSite, which Google promoted back in 2016 recently announced that it’d start pushing more aggressively in Chrome starting in July 2020.
Let’s dig into the use of SameSite cookie attributes and Chrome’s active warning signs today.
Explanation of SameSite Cookie Attributes
Adding SameSite support to Chrome requires web developers to control cookies using the SameSite attribute of the Set-Cookie header, which can be Strict, Lax, or None.
Using these attributes are a way of controlling which cookies can be sent by the browser and under what circumstances. Here’ s a quick explanation of each attribute value.
- STRICT: A cookie set to the ‘Strict’ value will not send cookies when a third-party issues the request.
- LAX: Setting ‘Lax’ will allow cookies to be made available to third parties via HTTP GET requests.
- NONE: The ‘None’ value simply allows a cookie to be accessed in the same way it is today.
Using these values, developers instruct browsers to control whether cookies are sent along with the request initiated by third-party websites by using the SameSite cookie attribute.
The thing to note about the SameSite attribute is that it can only be added to HTTP cookies, or cookies set on the server side.
With fewer cookies flying around, this will hopefully help the security and privacy of online users.
Google Chrome SameSite Warnings
If you’re an active Chrome user, you might be wondering about the warnings seen in the Console, such as the one below.
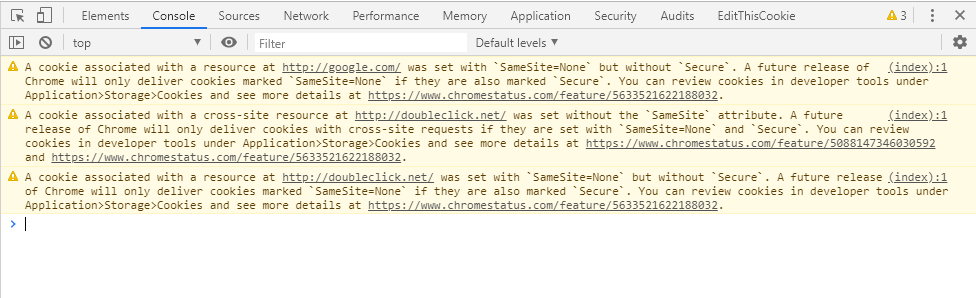
Google is beginning to warn website owners that in the near future they will enforce the use of SameSite attributes.
The warning introduced by Chrome version 76 pops up when a cookie is set with ‘SameSite=None’, but without ‘Secure’. The warning includes that there will be a future release of Chrome that only deliver cookies marked ‘SameSite=None’ if they are also marketing ‘Secure’.
Many current sites set cookies without a SameSite attribute, so it will take time for developers to start fully using them.
What to Do Now
If you’re seeing those warnings on your site, ensure that any cookies you set on the server side have the appropriate attribute. Then, if you continue to see the warnings, you will have to contact the vendor referenced in the warning to ensure they update the attributes on their cookie.
If you’re a CookiePro customer and see the warning related to onetrust.com, know that we are working with Cloudflare to ensure that their security _cfduid cookie, which is sent with our geolocation service, gets the SameSite attribute added.
Please reach out to [email protected] for any other questions.
You Might Also Like











